Asian ,Balkumari ,Gupteshwor ,HDC ,NCC ,ST Xavier ,Morgan ,IMS ,SDC,SPA ,


Asian
Why guard band are used in FDM? Asian pre board 2019
= Guard band as we know is the band of frequency to prevent the overlapping of channel and interference between the frequency among nearest channel. So, It is used in FDM To prevent overlapping of channel.
Define VSAT. Asian pre board 2019
= VSAT stands for Very Small Aperture Terminal which are fixed satellite terminals that are used to provide interactive or receive only communications.
List the private IP address ranges. Asian pre board 2019
= Private IP address are Class C IP addresses which ranges from
minimum: 192.0.0.0
Maximum: 233.255.255.255
What do you mean by piggy backing? Asian pre board 2019
= The techniques of temporarily delaying the outgoing acknowledgement and hooking it to the next outgoing frame is called “Piggy Backing”.
Why telnet protocol is needed? Asian pre board 2019
=Telnet is a protocol that allows you to connect to remote computers (called hosts) over a TCP/IP network (such as the internet). Using telnet client software on your computer, you can make a connection to a telnet server (that is, the remote host).That’s why telnet is needed.
Which layer devices are routers, switch, bridge and Hub? Asian pre board 2019
= A hub and switch is works on physical layer.
Bridge works on data link layer.
Routers works on Network layer.
Why we change IPV4 into IPV6? Asian pre board 2019
=We change IPv4 into IPv6 due to following reasons:
- Expanding routering and addressing capability.
- Header format simplification.
- Improve the quality of service capability (QS).
- Improve support for option.
- Authotenciation and Privacy capabilities.
List the transmission characteristics of digital system. Asian pre board 2019
= The transmission characteristics of digital system are:
- Less error
- High speed
- Digital flow of data etc.
Define socket and socket address. Asian pre board 2019
= Socket is used to establish a connection between two end points. It establish the connection logically or physically.
Socket address is the combination of port number and IP addresses. Port number define the services and IP address define the specific user, by counting them to establish the connect between two end points i.e. socket address= IP address+ Port number.
Differentiate between synchronous and asynchronous transmission. Asian pre board 2019
=
| Synchronous | S.N | Asynchronous |
| Synchronous transmission of data generally with the use of external clock signal . | 1 | Asynchronous transmission of data generally without the use of external clock signal . |
| No start or stop bits. | 2 | Start and stop bits are used for synchronization |
| Cheap , less hardware | 3 | Extensive , Complex hardware. |
Balkumari
Define multiple access and its types.
- Multiple access is a technique that lets multiple mobile users share the allotted spectrum in the most effective manner.
- The types of multiple access are as follows:
- Frequency division multiple access
- Time division multiple access
- Code division multiple access
What is frame relay? What are its needs?
Frame relay is often used to connect LANs with major backbones as well as on public area networks and also in private network environments with leased T-1 lines. It requires a dedicated connection during the transmission period and is not ideal for voice or video, which require a steady flow of transmissions.
What are the advantages of ipv6 over ipv4?
- The advantages of ipv6 over ipv4 are as follows:
- The ipv6 protocol has solved some , but not all, of the security problems found in ipv4 networks.
What is CSMA? Write down its types.
- Carrier sense multiple access(CSMA) is a network protocol that listens to or senses network signals on the carrier/ medium before transmitting any data.
- The types of CSMA are as follows:
- 1- persistent
- Non – persistent
- P- persistent
- O-persistent
Define SMTP. Write down advantage of IMAP over POP3.
- Simple mail transfer protocol(SMTP) is the standard protocol for email services on a TCP/IP network.
- The advantage of IMAP over POP3 are as follows:
- It is possible to manage local file from the server.
- It allows the search of message through keywords.
- Define DNS. List out difference between ARP and RARP.
- DNS is a hierarchical system, based on a distributed database, that uses a hierarchy of name servers to resolve internet host names into the corresponding IP addresses required for packet routing by issuing a DNS query to a name server.
The difference between ARP and RARP are as below:
| ARP | RARP |
| ARP stands for address resolution protocol. | RARP stands for Reverse address resolution protocol. |
| ARP is used to get the physical address of destination machine. | RARP is used to map the MAC address to corresponding IP address. |
List out the difference between ISDN and DSL.
- The difference between ISDN and DSL are as follows:
| ISDN | DSL |
| I. ISDN stands for integrated services digital network. | I. DSL stands for digital subscriber line. |
| II. It can integrate speech and data on the same lines, which were not available in the classic telephone system. | ii. It’s maintain the high speed of the internet being transferred. |
What is routing? Compare between static and dynamic routing.
- Routing is the process of moving packet across a network from one host to another.
- Static routing is a technique in which the administrator manually adds the routers in a routing table.
- Dynamic routing is a technique in which a router adds a new route in the routing table for each packet in response to the changes in the condition or topology of the network.
Define network topology. What are different modes of transmission?
- A network topology is a geometric arrangement of the computers in a network. It is also refers to the physical or logical layout of a network.
- The different modes of transmission are as follows:
- Simplex
- Half- duplex
- Full- duplex
What is multiplexing? Why multiplexing is needed for transmission ?
- Multiplexing is a technique used to combine and send the multiple data streams over a single medium.
- Multiplexing is needed for transmission because multiplexing is to enable signals to be transmitted more efficiently over a given communication channel, thereby decreasing transmission costs.
Gupteshwor


a.why signals are modulated before transmission?
= Modulation allows us to send a signal over a bandpass frequency range. If every signal gets its own frequency range, then we can transmit multiple signals simultaneously over a single channel, all using different frequency ranges, so signals are modulated before transmission.
b.what are the advantages of using optical fibre?
= they are;
- Low transmission rate
- Rigidless and flexible
- Enormous potential bandwidth
c.What are the advantages and disadvantages of guard band in fdm?
=its advantage is that it is used to avoid interference between two channel,and disadvantage is that it is unused freguency .
d.what is the most vulnerable component in basic data communications model and why?
=Transmission channel is the most vulnerable component in basic data communications model because it is the part where noise and distortion easily affect.
e.define frame synchronization.
=It is amethod of finding valid data in the transmission of the frame.
f.how shortest path can be guaranteed in flooding routing algorithm?
= Flooding is a simple routing technique in computer networks where a source or node sends packets through every outgoing link. … Because flooding uses every path in the network, the shortest path is also used. The flooding algorithm is easy to implement.
h.state any improvement in IPV6 as compared to IPV4?
= Advantages of IPv6 over IPv4 :
- Larger Address Space.
- Better security for networks and applications.
- Better connectivity.
- Quality of Service (QoS)
- Data Integrity is improved.
i.differentiate between SMTP and POP?
= The key difference between SMTP and POP is that SMTP is a message transfer agent and POP is message access agent.
j.List two functions of BSD Socket API?
=they are send() and recv().
Himalyan

Why signals are modulated before transmission?
Ans: Signals are modulated before transmission is to travel long distance, to allow the use of a smaller antenna.
- What are the advantages of using optical fiber?
Ans: The advantages of using optical fiber are:
- High bandwidth
- Reliable
- What is the purpose of piggybacking?
Ans: The purpose of piggybacking is simply to gain free network access rather than any malicious intent, but it can slow down data transfer for legitimate users of the network.
- How does ARQ corrects errors?
Ans: ARQ corrects errors by using acknowledgement.
- Which multiplexing is preferred in digital transmission and why?
Ans: TDM multiplexing is preferred in digital transmission because it is used for long-distance communication links and bears heavy data traffic loads from end users.
- Why ARP protocol is required?
Ans: ARP protocol is required to change logical address to physical address.
- What is function of TTL FIELD?
Ans: The function of TTL field is that it tells a network router whether or not the packet has been in the network for too long and should be discarded.
- Why do you do CIDR?
Ans: CIDR (Classless inter-domain routing) is used to create unique identifiers for networks and individual devices
- Which protocols and respective ports are used for sending and receiving emails?
Ans: SMTP and POP are used for sending and receiving emails.
- List the various ranges of private IP address.
Ans: The various ranges of private IP address are:
Class Private IP Address Range Subnet Mask
A 10.0.0.0 to 10.255.255.255 255.0.0.0
B 172.16.0.0 to 172.31.255.255 255.240.0.0
C 192.168.0.0 to 192.168.255.255 255.255.0.0
NCC

- Define super-netting?
- Super-netting, also called Classless Inter-Domain Routing (CIDR), is a way to aggregate multiple Internet addresses of the same class. The original Internet Protocol (IP) defines IP addresses in four major classes of address structure, Classes A through D. Each class allocates one portion of the 32-bit Internet address format to a network address and the remaining portion to the specific host machines within the network.
- List out the phases in correction-oriented service.
- They are:
- Setup phase
- Data transfer phase
- Teardown phase
- They are:
- Define Token Ring.
- Token Ring is alocal area network(LAN) technology is a communications protocol for local area networks. It uses a special three-byte frame called a “token” that travels around a logical “ring” of workstations or servers. This token passing is a channel access method providing fair access for all stations, and eliminating the collisions of contention-based access methods.
- Why is ARP and RARP protocol used?
- Address Resolution Protocol (ARP) is a protocol that helps IP to find the link-layer address of a host or a router when its network-layer address is given. Reverse ARP (RARP) works opposite of ARP.
- Define fixed path routing.
- A route is selected for each source-destination pair of nodes in the network. The routers are fixed and changes only if topology of the network change. It is something referred to as static routing since the routes are fixed as in static routing.
- Differentiate between OSPF and BGP?
- Some of the key differences are:
- The OSPF stands for Open Shortest Path First whereas BGP expands to Border Gateway Protocol.
- OSPF is an Interior gateway routing protocol in which the routing operation is performed inside an autonomous system. On the other hand, the BGP is an Exterior gateway routing protocol which enables the routing operations to be performed between the two autonomous systems.
- OSPF is simple to employ while BGP is complex to implement.
- The time elapsed by a router takes to share and update the latest routing information is known as convergence. So, OSPF can achieve convergence by consuming less time. In contrast, the BGP has a slow convergence rate as compare to OSPF.
- The OSPF follows a hierarchical structure whereas BGP usually adopts mesh structure.
- OSPF requires intensive use of memory and CPU resources. As against, in BGP the need of device resources relies on the size of the routing table.
- BGP is more flexible and scalable than OSPF and used on a larger network, unlike OSPF.
- The primary objective of the OSPF is to determine the best route, i.e., fastest. Conversely BGP emphasizes on determining the best path.
- OSPF uses link state routing while BGP uses path vector routing.
- Some of the key differences are:
- What is the necessity of Port address even if there is IP address for the device?
- To put it simply, IP address are to identify the hosts and port numbers are to identify/differentiate type of services on the hosts. If we’ve reached the destination host, the next thing we need to tell your destination is the type of service we are looking for, such as email, web etc., which are identified/differentiated by port numbers or port address.
- What is the difference between DSL and ADSL?
- DSL(Digital Subscriber Line) is the generic term for services that provide internet connections using digital data connections between a modem and a phone line. What’s great about DSL, is that even when the phone line is in use, there is no interruption, and you can still experience a high speed internet connection even when you are making calls.
- ADSLstands for Asymmetric Digital Subscriber Line. This type of service means that the speed of data sent is known as upstream, and the data received is known as downstream, and the speeds are not always guaranteed to be the same. They have different speeds that change from time to time. The most requested service is the ADSL service. In regards to ADSL, the internet service providers offer options for higher bandwidth, in upstream, downstream or both. The only thing is, they naturally charge higher rates for higher speeds.
- What is the advantage of SMTP over IMAP?
- SMTP provides the notification of the delivery of the message when it is sent, along with this it also provides with the error when found any.
- What is the common subnet mask for the following addresses: 192.168.3.56, 192.168.1.1, 192.168.5.127?
- The common subnet mask of the given addresses is 22.
SPA
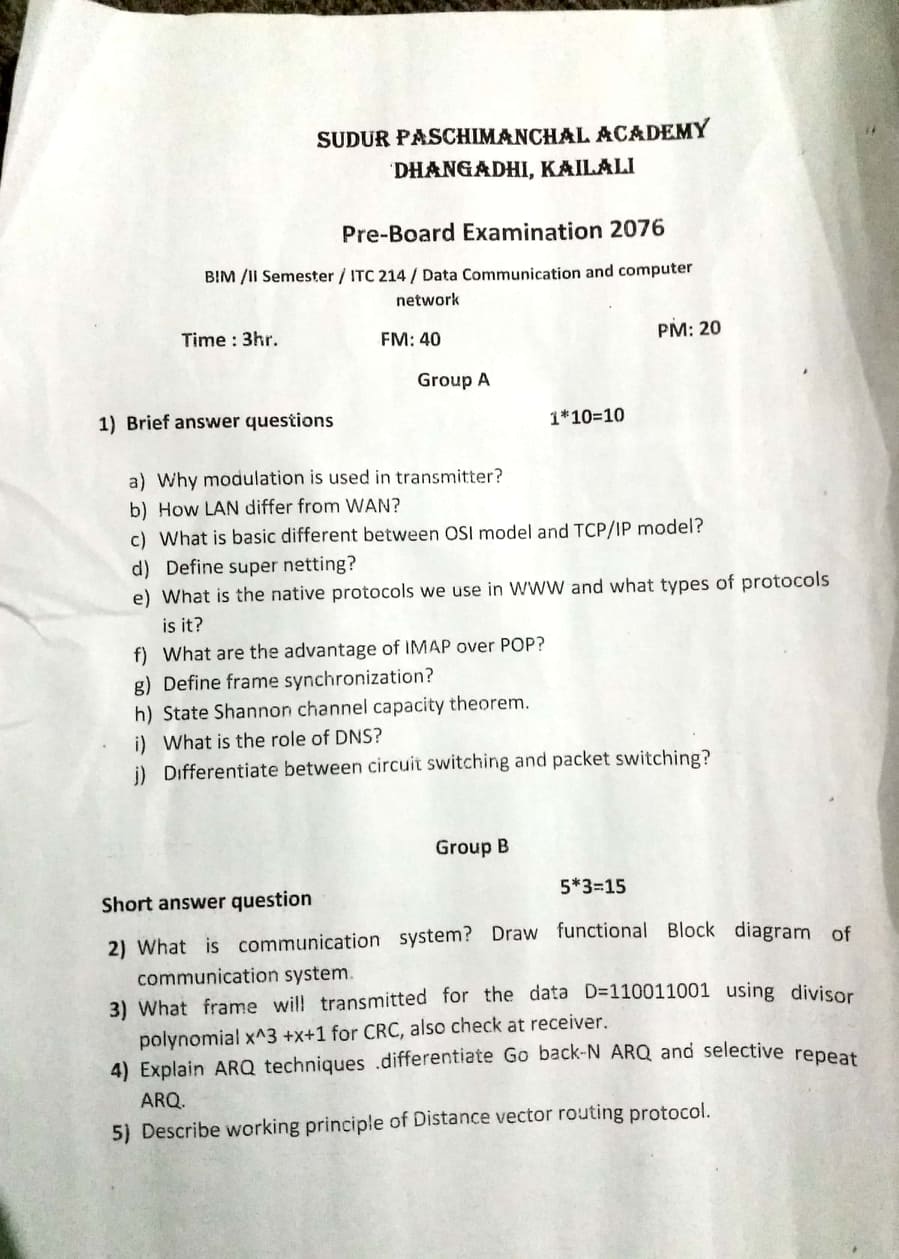

Why modulation is used in transmitter?
Ans:- The message frequency is too low to travel and reach the destination because the losses are too much during the transmission so, we modulate it into higher frequency carrier and send it for long distance transmission.
Define Super netting?
Ans:- Supernetting, also called Classless Inter-Domain Routing (CIDR), is a way to aggregate multiple Internet addresses of the same class.
What is the Native Protocal we used in WWW?
Ans:- HTTP and HTTPs are the native protocol used in WWW.
What are the advantages of IMAP over POP?
- Robust folders for storing received and sent messages
- Freedom for user to download attachments at will
- Provision for determining message structure without downloading entire message.
- Selective fetching of individual MIME body parts.
- Server-based searching and selection to minimize data transfer.
- Ability to append messages to a remote folder.
Define frame synchronization?
Ans:- Frame synchronization or framing is the process by which, while receiving a stream of framed data, incoming frame alignment signals (i.e., a distinctive bit sequences or syc words) are identified (that is, distinguished from data bits), permitting the data bits within the frame to be extracted for decoding or retransmission.
State Shannon capacity theorem?
Ans:- The Shannon–Hartley theorem states the channel capacity C is equals to
C=Blog2(1+SN)
Here C is the maximum capacity of the channel in bits/second otherwise called Shannon’s capacity limit for the given channel, BB is the bandwidth of the channel in Hertz, SS is the signal power in Watts and NN is the noise power, also in Watts. The ratio S/NS/N is called Signal to Noise Ratio (SNR).
What is the role of DNS?
Ans:- The main function of DNS is to translate domain names into IP Addresses, which computers can understand.
St xavier
i.Domain name are the mnemonic form of the IP address. Since ip address are string of numbers they are difficult to remember so domain name are used for our convenience.
In reliable full – duplex data transmission, the technique of hooking up acknowledgments onto outgoing data frames is called piggybacking.
v.PSK modulation technique are better than FSK and ASK modulation in terms or bandwith requirements.
the function of
ICMP :
ICMP is used for reporting errors.
IGMP:
IGMP reports to routers about the membership status to host.
viii the unreliable protocol is UDP. It is named so because UDP does not establish a connection between host and destination before data transmission
ix .subnet mask is done because A subnet mask defines the IP addresses that can exist within a specific subnet, such as a local area network. It has a similar appearance to an IP address, but it “masks” the network part of the IP address.
Morgan
- Difference between bit rate and bud rate?
the number of bits per second that can be transmitted along a digital network is called bit rate.
Ans: The rate of transmitting the signal element including the bit required for synchronization.
- Least the characteristics of signal?
Ans: analog signal: analog signal is the signal which is continiou in state.
Digital signal is the signal which is descrete in state.
- What is channel capacity?
Ans: channel capacity is the rate which data can be transmitted over a given communication channel given a condition.
- Least the application of satellight?
Ans: satellights are used for television , telephone radio ,internet and military application.
- Difference between physical and logical topologies?
Ans: physical topology refer how a network look and function and logical topology fashion in which data travel logistical
Physical topologies are bus ,star ,ring and mess ,logical topologies are logical bus and logical ring.
- Least the features of wireless communication?
Ans: cost effectiveness ,feasibility ,convenience ,speed ,assesibility ,constant connectivity.
- What is bridge?
Ans: A bridge is a type of computer network devices that provides interconnection with other bridge network that use same protocol.
- What is supernet?
Ans: it is an internet network protocol network that formed for routing purpose from the combination of two or more network.
- Define DSL,POP?
Ans: DSL is a family of technique that used to transmit the data over telephone lines
POP is an access point from one point from one place to rest of the internet.
- Define FQDN.
Ans: A fully qualified domain name sometimes also refered to an absolute domain name it is the domain name which specifies its exact location in hierarchy in domain system.









Terminal 2019
Asian ,HDC Inderni Kanya NCC NISt
Asian
What do you mean by data communication?
Ans: Data communication refers to the exchange of data between a source and a receiver via form of transmission media such as a wire cable. Data communication is said to be local if communicating devices are in the same building or a similarly restricted area.
Why guard band are used in FDM?
Ans: Guard band is the unused frequency created in the bandwidth which is used to prevent the overlapping of frequency or data and prevent them from collapsing.
In what case analog signal is preferred than digital signal?
Ans: In real time measurement and for minimum bandwidth requirement analog signal is preferred than digital signal.
How does NRZ-L differ from NRZ-I?
Ans: In NRZ-L positive voltage is assigned for one symbol and negative for another whereas in NRZ-I ‘1’ symbol inverts the polarity and ‘0’ does not.
What are the major responsibilities of network layer?
Ans: The major responsibilities of network layer are:-
- Packet encapsulation
- Packet filtering
- Fragmentation
Define spectrum.
Ans: spectrum means the range of frequency that the signal exist.
Write any three advantage of optical fiber cable?
Ans: Any three advantages of optical fiber cable are:-
- It has high bandwidth
- Low signal loss
- It is low costly and flexible
Define WDM.
Ans: WDM is an analog multiplexing technique to combine optical signals.
Define VSA
ANS: VSAT are fixed satellite terminals that are used to provide interactive or receive only communication.
What is the main principle of layering of osi model?
Ans: The main principle of layering of OSI model is control is passed from one layer to next.
HIMALAYA DARSHAN COLLEGE
What is most vulnerable component in basic data communication model and why?
Ans: The most vulnerable component in basic data communication model is the channel, a physical medium which converts the transmitter and receiver because as the signal passes through the channel it may deteriorate through various impairments.
What are the disadvantages of computer network?
Ans: the disadvantages of computer network are:
- Security is the major issue
- It may be expensive
What are the advantages and disadvantages or guard band in frequency division multiplexing?
Ans: Guard band prevents the overlapping of various channel in FDM.it is one of the advantage whereas the disadvantage is that it occupies more bandwidth.
What is signal?
Ans: A signal is defined as an electromagnetic current that is used to carry data from one network or device to another. It is simply flow of information.
Difference between Analog signal and Digital signal.
Ans:
| Analog signal | Digital signal |
| i. It is continuous signal. ii. Amplifiers are used to boost analog signal. |
It is discontinuous signal. Repeaters are used to boost digital signals. |
What is Transmission impairments?
Ans: In a communication system, signal propagates analog transmission media, it gets deteriorated by various factors. The imperfection is called transmission impairments.
Compare Synchronous and asynchronous transmission.
Ans: In synchronous transmission data is transmitted in form of chunks while in asynchronous data is transmitted one byte at a time. Data transfer rate of synchronous is faster as compared to asynchronous transmission .
What is SNR?
Ans: SNR stands for signal to noise ratio. It is the power of signal to the power of noise. It should be more than 1db.
Indreni
Define synchronous transmission.
- Synchronous transmission refers to the transmission in which data flows in a full duplex mode in the form of blocks or frames. Synchronization between sender and receiver is necessary so that the sender know where the new bytes starts.
How does NRZ-I differ from NRZ-L ?
In NRZ-L two different voltages is provided for 0 and 1 bits but in NRZ-I constant voltage pulse for duration of bit time.
What are the network support layer and user support layer in OSI model ?
The network layer in OSI model are layer 1, 2, 3 and user support layer are layer 5, 6, and 7.
In what case analog signal is preferred then digital signal ?
If you need continuous data and for the long distance analog signal is preferred then digital signal.
List the basic characteristics of the signal.
- The basic characteristics of the signal are:
- Signal amplitude
- Signal phase
- Frequency fact
- Wavelength information
What are the advantages of using optical fiber ?
- The advantages of using optical fiber are as follws:
- Faster in speed i.e. 1GHz
- No crosstalk
- Reduced size and weight of cable
- Higher data transmission rate
How LAN differ from WAN ?
| LAN | WAN |
| · Local area only i.e. school, college etc. | · Large geographic area i.e. cities,nation etc. |
| · High speed (1000 mbps) | · Low speed (150 mbps) |
| · High data transfer rate | · Low data transfer rate |
| · High bandwidth is available for transmission | · Low bandwidth is available for transmission |
What is the difference between error rate and data rate ?
| Error rate | Data rate |
| · It is the number of bit error per second. | · It is the number of bit transferred per second. |
| · If error rate is higher then communication will be slow. | · If data rate is higher then communication will be fast. |
Kanya
Which is the most vulnerable component in the basic communication model and why?
Ans: Communication channel is most vulnerable component in basic data communication because different factor like noise, distortion may affect the quality of signal.
Which layer is responsible for end to end reliable transportation?
Ans: Transport layer is responsible for end to end reliable transmission.
Define synchronous transmission.
Ans: Synchronous transmission is an efficient method of transferring large blocks of data by using time intervals for synchronization.
What are the connectors used in fiber optical cable?
Ans: Connectors used in fiber optical cable are-
- Sc ( subscriber connector)
- ST ( straight tip/connector)
How LAN is differ from WAN?
Ans: LAN is designed to operate over a small physical area such as office, school etc where WAN is designed to operate large geographical area that may comprises a country or continent.
State Shannon’s channel capacity.
Ans: Maximum amount of information that can pass through a channel without error is called Shannon’s channel capacity.
Channel capacity =B
Which multiplexing is used for pure analog data transmission?
Ans: Frequency Division Multiplexing (FDM) is used for pure analog data transmission.
If a spectrum of signal is 11mhz to 34.5mhz find a bandwidth occupied by a signal?
Ans: Bandwidth of a signal = ( 34.5-11) mhz =23.5 mhz
What are the possibilities of the transmission of frames in stop and wait ARQ method?
Ans: The possibilities are
- Lock ACK
- Delayed ACK
- Damaged ACk
What is the main limitation of parity check method?
Ans: Parity check method can’t handle the even number of 1 changed i.e. 2,4,6,8 etc. which is its main limitation.
NCC
How LAN is different from WAN?
Ans:-LAN(Local Area Network)is the transmission medium or media which covers only the certain distance.It is suitable for the house ,building,office.
WAN(Wide Area Network)is the type of network which covers the geographical area or country.It is used in the form of satellite.Specially it is used to transmit network.
List out different types of transmission media.
Ans:-The different types of transmission media are;
i.Guided media-Twisted pair,Co-axial cable,Fiber-optic cable
ii.Unguided media-Radio waves,Microwaves
What is the basic difference between OSI Model and TCP/IP Model?
Ans:-The basic difference between OSI model and TCP/IP moel are;
| OSI model | TCP/IP moel |
| -OSI model is independent. | -TCP/IP model is dependent. |
| -It has 7 layers. | -It has 4 layers. |
| -It is connection oriented. | -It is connectionless or connection oriented. |
What are the fundamental characterstics of data communication?
Ans:-The fundamental characterstics of data communication are;
- Delivery
- Accuracy
- Timeliness
- Jitter
What are the criteria that network must meet?
Ans:-The criteria that the network must meet are;
i.Performance
Reliability
iii.Accuracy
Define digital transmission and analog transmission.
Ans:-Digital transmission is the transmission of signals that vary discretely with time between two values of same physical quantity and it is the transmission of signal in which there is not continuous flow of signal.
Analog transmission is the transmission using continuous signal and which varies in amplitude,phase,frequency or other properties.
What are the characterstics of analog signal?
Ans:-The characterstics of analog signal are;
i.Amplitude
ii.Frequency
iii.Phase
IV.Period
Define propagation delay.
Ans:-Propagation delay means the delay in receiving the data or it is the condition in which ata send by the sender cannot be received by the receiver in the specific time period.
NIST
Why are signals modulated before transmission
Modulation allows us to send a signal over a bandpass frequency range. If every signal gets its own frequency range, then we can transmit multiple signals simultaneously over a single channel, all using different frequency ranges so signals are modulated before transmission.
What do you mean by serial transmission?
Serial trasmisson is the process of sending data one bit at a time, sequentially, over a communication channel or computer bus.
Define attenuation.
Attenuation means reduction of strength of signal during data transmission.
What do you mean by network topology?
Network topology means the layout or how the computers are connected to each other’s in a network.
Define VSAT
VSAT (Very Small Aperture Terminal) is a is a two-way satellite ground station with a dish antenna satellite communications system that serves for home and business users.
What are the advantages of optical fiber cable?
- It has higher bandwidth than other medium
- It has higher speed than other medium
- It is lighter than other medium
- It has less data loss than other medium
- What are the advantages of satellite communication over other communication media?
The advantages of satellite communication medium over other medium are as follows
- It covers wide area of the earth hence entire country or region can be covered with just one satellite.
- Wide area of application such as whether forecasting ,search ,navigation, military.
- Satellites have average low operating cost. Manufacturing of satellite is expensive but after that it would operate typically for years.
- Mobile communication is easy to achieve using satellite communication because of its broader coverage area and its flexibility in connecting mobile vehicles.
- SNR of a signal is 20db. What does it mean?
The SNR of a signal is 20db means it is 100 times more powerful than noise.
Pre board 2018
CAB
1. Write the formula to calculate the capacity of noiseless channel.
The formula to calculate the capacity of noiseless channel is C = 2Blog2l where C is the capacity in bps, B is the bandwidth and L is the level.
2. Define the term SNR.
SNR or Signal to Noise Ratio I the ratio of signal strength of a medium to the noise present on the medium.
3. List all the framing techniques.
The framing techniques are
- Character Count
- Character Stuffing
- Bit Stuffing
- Physical Code Violation
4. Why is router called layer 3 device?
A router is called a layer-3 device because it is used in the 3rd layer of OSI model i.e Network Layer and handles layer-3 IP packets.
5.How can we handle the problem of signal attenuation during transmission?
A. We can handle the problem of signal attenuation during transmission by using devices like Repeater or Amplifiers.
6. In which scenario flooding is used?
Flooding is used in the network layer when the data is to be sent to every router or node in the computer network.
7. Why do we need to create supernets?
We need to create supernets to combine multiple networks into a bigger network which reduces the size of routing tables thus making the network faster.
8. What is VCI?
A. A virtual channel identifier (VCI) distinguishes virtual channels (also known as circuits) created in a packet/cell switched network
9. List the application area of UDP.
The application area of UDP are live broadcast, video calling etc.
10 .Define the term VoIP.
VoIP (voice over IP) is the transmission of voice and multimedia content over Internet Protocol (IP) networks.
Kist
1.In what case analog signal is preferred than digital signal?
analog signal is preferred than digital signal because of following reasons:
- the cost is comparatively lower than that of digital signal.
- Suitable for short distance transmission due to lower cost.
- Analog components are durable.
- Processing can be done in real time system
2.Define VSAT.
VSAT is a satellite technology that uses transceiver in each end user to communicate that interfaces between the user’s computer and an outside antenna with a transceiver. The transceiver receives or sends a signal to a satellite transponder in the sky. In VSAT technology satellite acts as a HUB i.e. similar to that of star topology and helps in communication among various parts of the world.
3. What do you mean by Piggybacking?
In sliding window flow control technique, the system works in full duplex mode. So in order to communicate in both the direction there is needed to maintain two window to send data and acknowledgement to other side. To provide efficient support piggybacking technique is used.
Piggy backing is a technique that is temporary outgoing delay of acknowledgement so that it can be hooked up with next outgoing frame. Each frame consists of serial no and acknowledgement number. Piggy backing is used for proper communication channel utilization.
4.Why telnet protocol is needed?
Telnet is a terminal program run on a client computer and connect to server on network. Client can enter the command through telnet program to enter the server. This enable client to control the server by enabling valid username and password. Telnet is the common way to remotely control webserver.
5.Define socket and socket address.
Sockets is used to establish connection between two endpoints. It helps to establish connection logically or physically. Basically we use Application Programming Interface to establish connection between two processes.
Socket address is the combination of port number and ip address. Port number define the services and Ip address define a specific host. By using these information socket establishes the connection between two endpoints.
6.List the internet control protocols.
The internet control protocols are: 1.ICMP 2.IGMP
7.List the private ip-address ranges.
The list of private ip-address ranges are:
- 0.0.0to 10.255.255.255 —Class A
- 172.16.0.0 to 172.31.255.255—-Class B
- 192.168.0.0 to 192.168.255.255—-Class C
8.Why we change ipv4 into ipv6?
Ipv4 consists of 32 bit address and have some limited features but the ipv6 can address 64 bit and can connect more devices in the network as well as helps in allocating address, making improvements to ease the routing of packets, and makes it easier to configure a machine so we change ipv4 to ipv6.
9.List the transmission characteristics of digital system.
=> The transmission characteristics of digital system are:
- Can transmit data at very high speed
- High service integration.(AUDIO,VIDEO,TEXT)
- Reliable, fast and efficient.
- Provides more security.
- High noise immunity.
- New Technology.
10.Difference between Synchronous and asynchronous transmission.
| Asynchronous | Synchronous |
| 1. Data is transmitted Character by Character and each character is of 8 bit length. 2. It requires overhead of two bit for transmission of data. 3. If a frame is lost then it cannot be recovered. 4. Suitable for low speed transmission. |
1.It doesn’t require overhead of two bit for transmission of data. 2.For data transmission transmitter sends synchronous pulse and when receiver locks it a block of data gets transmitted. 3.Lost of frame is found to be low and can be recovered. 5. Suitable for short distance transmission. |
Orchid SET B
(i) What is baud rate in data communication? Explain.
Baud rate in data communication refers to the amount of data transmitted over a channel in a fixed amount of time.
(ii)What is the task of presentation layer in networking?
The task of presentation layer in networking is to convert the data into an appropriate format at the sender's side and change the received data into actual format at the receiver's side.
(iii) Explain selective repeat protocol.
While sending the messages from one host to other, some frames may not reach or may contain error, in such cases the receiver asks the sender to send only specific frames again, this process is known as selective repeat.ount of time.
(iv) Differentiate between CSMA/CD and CSMA/CA protocol.
CSMA/CD refers to carrier sense multiple access/ Collision detection protocol that can sense the channel before transmitting the message and can also detect if any two data collides whereas CSMA/CA refers to carrier sense multiple access/ Collision Avoidance
protocol that can sense the channel as well as other senders, which helps in avoidance of data collision.
(V) Explain the virtual circuit approach for packet switching.
The virtual circuit approach for packet switching includes three steps:
– Virtual connection setup
-Data transmission
– Virtual Circuit termination
Here, first a virtual connection is setup and then actual data is transmitted and then the circuit is terminated.
(vi) List out the difference between IPv4 and IPv6.
The main difference between IPV4 and IPV6 is that IPV6 has comparatively larger no. Of UP addresses than IPV4.
(vii) State the principle of Distance-Vector Routine protocol.
The distance-vector routing principle states that the path having minimum no. Of hop counts will be used for the data transmission over a network.
(viii) Clarify on sequence Number and Acknowledgement Number used in TCP header
The sequence no. Determines the sequence no. of the frame whereas the acknowledgement no. determines the no. Of frames and its acknowledgement which has been received by the receiver.
(ix) Differentiate between HTTP and FTP protocol.
FTP is used to send, upload and download files over a network whereas HTTP is used to request for different web pages, sites, etc over a network.
(x) What is the use of NFC? Explain.
The use of NFC is to create a small private networks over which different regular works like payments, fund transfer, etc can be done.
NCC
Qn.2 answer:
HTTP is called a stateless protocol, which means that the connection between the browser and the server is lost once the transaction ends.
Qn.3 answer:
- Class A: 10.0.0.0 – 10.255.255.255
- Class B: 172.16.0.0 – 172.31.255.255
- Class C: 192.168.0.0 – 192.168.255.255
Qn.4 answer:
Solution: Highest frequency:
1MHz=1000KHz
1.75MHz=1750KHz
Lowest frequency:
1.03KHz
We know,
Bandwidth= Highest frequency-lowest frequency
=(1750-1.03)KHz
=1748.97KHz
=1.74897MHz
Qn.5 answer:
Port number is used as a transport layer address to choose among multiple processes running on the destination host.The range of port number:
- Well known port: 0 – 1,023
- Registered port: 1,024 – 49,151
- Dynamic port: 49,152 – 65,535
Qn.6 answer:
In a synchronous time division multiplexing, most of the time slots in a frame are not being utilized, whereas no space is wasted by statistical time division multiplexing.
Qn.9 answer:
Switching is process to forward packets coming in from one port to a port leading towards the destination.Routing refers to establishing the routes that data packets take on their way to a particular destination.
Qn.10 answer:
SMTP (Simple Mail Transfer Protocol) is a TCP/IP protocol used in sending and receiving e-mail which is a simple ASCII protocol for sending image, video, Unicode etc.
MIME (Multi-Purpose Internet Mail Extensions) is an extension of the original Internet e-mail protocol that lets people use the protocol to exchange different kinds of data files on the Internet: audio, video, images, application programs
NCCS
1. What are the three fundamental concepts of data communications?
Ans: The three fundamental concepts of data communications are:
a. Destiny.
b. Reliability
c. Fast
2. Difference between DTE and DCE
Ans: The difference between DTE and DCE is
DTE: It stands for Data Terminal Equipment which generates the data stream. Eg. PC ,end user
device.
DCE: It stands for Data Communication Equipment which plays the interface role between the
source and the medium and the destination.Eg. Modem, Router
3. Write the advantages and disadvantages of ADSl
Ans: The advantage of ADSL is:
a. We can use phone for voice calls and internet.
b. Digital data is directly transmitted to computer.
The disadvantages are:
a. It lacks speed during transmission.
b. Connection is distruped when far from central office.
4. What are the service provided by transport layer of OSI layer?
Ans: The service provided by transport layer of OSI layer is it provide communication services between computers in a network.
5. Why Guard bands are used in frequency multiplexing?
Ans: Guard bands are used in frequency multiplexing because it helps for the separation of channel
and ensures that the channel doesn’t interfare with each other.
6. What are the advantages of IMAP over POP?
Ans: The advantages of IMAP over POP is Two-way communication between the mail server and the e-mail client, which allows several devices to work on the same account seeing the changes made by all.
7. Why subnetting?
Ans: Subnetting helps to maintain clean separations within a network. For example, we can define boundaries between different departments in an organization, with one subnet for sales, another for marketing, and a third for production.
8. List any two functions used in BSD socket API?
Ans: The two functions used in BSD socket API are:
a. Socket()
It creates a socket and returns a refrence number for that socket.
b. Bind()
It associates a socket with a particular local port of IP address.
9. What are the attributes of good routing algorithm?
Ans: The attributes of good routing algorithm are:
a. Routers constantly monitor the condition of the network, as a whole to dynamically adapt to
changes in the condition of the network
b. It should have properties like correctness,simplicity,robustness,stability,fairness,optimiability.
